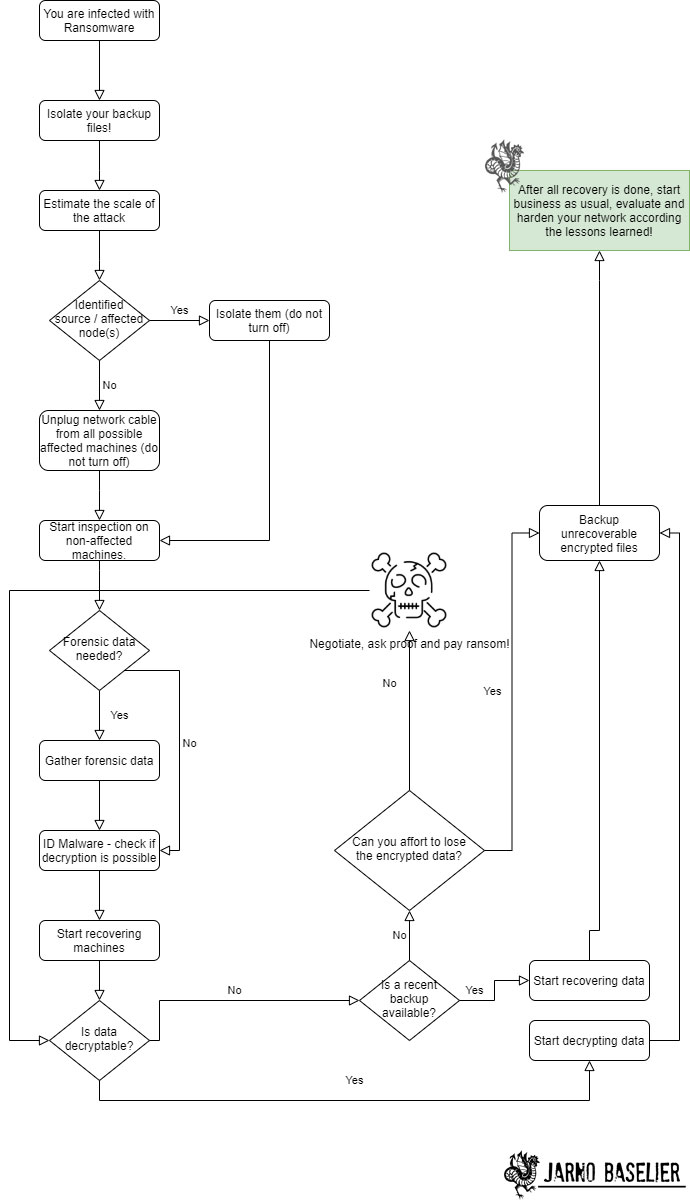
ToDo After Ransomware Infection / Attack (checklist)
Technical Team(s)
- Isolate your backup files and make sure the ransomware cannot touch it.
- Estimate the scale of the attack and the source node(s).
- Isolate the source node and all affected nodes. If the above step takes too long just pull the network cable from all affected machines (do not turn them off).
- Start inspection on the non-affected nodes (to be sure).
- Gather forensic data from the source node(s) if there might be a need for later in the process.
- ID the malware and check if there is a public decryptor available: Check ID Ransomware.
- Make a choice - Reinstall the machines completely or try to remove the ransomware (tools like Hitman Pro / Malwarebytes can usually assist you). After the choice is made, start the work.
- After machines are recovered start recovering your data (from backup or from decryption). Make sure that the machines you recover to are not infected with the ransomware (otherwise data will be encrypted again).
- Backup ALL encrypted data the you need and is not recoverable at the moment. Hope for a decryption solution in the future!
- WORST-CASE-SCENARIO: you have no backup and the encryption is not reversable. In this case you need to make a decision about the impact on the company. Can you start over without damaging the company too much… or can you simple not function anymore without the data? If the last answer is “yes” you need to think about paying the ransom. My advice is NEVER PAY RANSOM (and support these criminal activities) but in some cases there is simply no choice. Get in contact with the criminals and agree to a lower price (usually there is room for negotiation). Also ask for a sample of decryption before you pay.
- After recovery is done and tested restart the business. Then take the time to evaluate with professionals and act according the lessons learned. Start hardening your network.
Technical Flowchart:
Incident Response Coordination
- Start the Incident Response Procedure.
- Assign key persons / roles.
- Arrange technical assistence that you guess will be needed during the crisis (Forensic investigators, negotiators, technical expertise etc.).
- Communication is vital in this process. Make a plan to communicate efficiently.
- When the scale of the ransomware attack is known start reporting to the authorities (always try to report within 4 hours even if the scale is not completely known).
- Make sure everybody knows what to do and keep communication to your employees.
- Make a plan to get in contact with the criminals (in case this is needed).
- Take care for the technical team! They are under a lot of stress. Make sure they eat, drink and sleep well!